Human rights defenders and other vulnerable groups rely on independently developed open source security tools to provide safe and free software to protect themselves and their communities. In regions facing censorship and internet shutdowns, open source tools provide an essential service by enabling information sharing and privacy protection.
However, much of the most widely used and popular open source software is surprisingly fragile and under resourced. Moreover, the community maintaining these tools is plagued by the same diversity problem found in the wider tech industry. In a 2017 survey of open source community members, Github – the world’s largest repository for open source code – found that 95% of respondents were male. With most open source tools run on a volunteer basis, the privilege of having both the time and resources to contribute to open source projects is largely found in Western and high-income white communities.
Internews’ BASICS project (Building Analytical and Support Infrastructure for Critical Security tools) takes these two problems in the open source internet freedom community – sustainability challenges and lack of diversity – and combines them in order to solve both. BASICS is improving the sustainability of critical open source privacy and security tools by building ties between tool teams and the communities they serve and identifying privacy-conscious methods to track tool usage and prioritize development needs. To ensure that the tools BASICS will support are relevant and useful, the team conducted a market analysis to identify the most well-known and commonly used tools among at-risk communities.
Unlike traditional market analyses, the BASICS Market Analysis assumes that readily available user data and market trends are at least partially inaccurate. This is because vital but small tools may float under the public radar, while well-established tools occupy an oversized space. Because there are no existing reliable sources of data to indicate how widely any given tool is used (in addition to the self-reporting challenges that the BASICS project is designed to address), the market analysis primarily looked at 12 different digital security guides recommended by the OrgSec community to determine a tool’s usage within the market.
However, even widely used tools are often not promoted in traditional digital security resources for fear that they may lack longevity, as unmaintained tools pose a significant security risk for those who continue to use them. Tools may also be “used” only during specific times of need – for example, during an internet shutdown – but are absolutely critical to the communities facing limited information channels.
Digital security guides used in the Market Analysis
- Saferjourno – Internews
- Security in a Box – Tactical Technology Collective and Front Line Defenders
- Freedom of the Press Foundation Guide on Open Source Software
- Security Self Defense – The Electronic Frontier Foundation
- Digital First Aid Kit – RaReNet (Rapid Response Network) and CiviCERT
- Digital Safety Manual – Digital Defenders Partnership
- Journalist Security Guide – Committee to Protect Journalists
- Me and My Shadow – Tactical Technology Collective
- Security Planner – Citizen Lab
- Trainers’ Curriculum – LevelUp
- The Tow Center for Digital Journalism Reports – Columbia Journalism Review
- Safety Guide for Journalists – Reporters Sans Frontieres
Ashley Fowler, the USABLE teams lead at Internews, explained:
“INCREASINGLY, DIGITAL SECURITY TRAINERS AND OTHER PRACTITIONERS ARE MOVING AWAY FROM TOOL-SPECIFIC TRAINING, OPTING INSTEAD TO FOCUS ON GENERAL SECURITY CONCEPTS AND USER BEHAVIORS. THE FRAGILITY OF OPEN SOURCE PRIVACY AND SECURITY TOOLS MAKES IT DIFFICULT TO MAKE LONG-TERM TOOL RECOMMENDATIONS, AS THERE IS NO GUARANTEE THAT CURRENT TOOLS WILL CONTINUE TO BE MAINTAINED AND UPDATED.”
To address this challenge, the BASICS team also disseminated a “Suggested Tools” form as an open call to Internews’ broader organizational security and human rights network to gauge which tools the community are using. Responses came from developers and non-profits that are current or past Internews partners and were included in the Market Analysis.
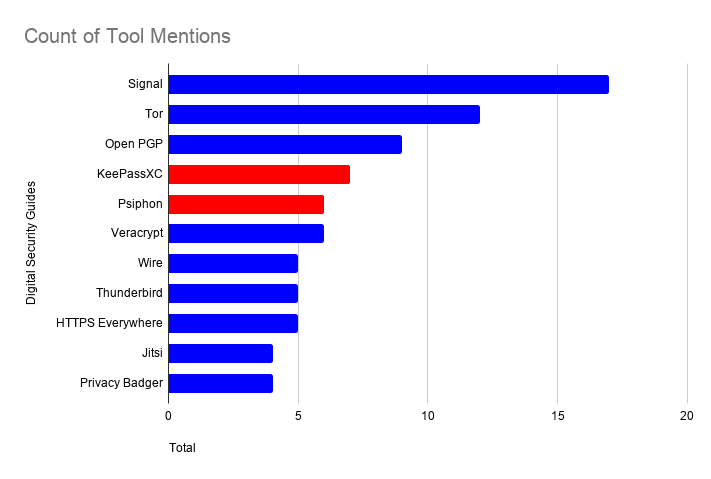
We found that secure communication (e.g. Signal, OpenPGP), secure browsing (e.g. Tor, HTTPS Everywhere) and password protection (e.g. KeePass XC) are the security needs most often cited in digital security guides. However, while there is an active and vibrant community of developers and designers committed to the creation and maintenance of open source tools, many of the guides that educate people on digital security are not regularly updated. Current tools that not only record consistent usership but were identified as commonly used among at-risk communities are often not spotlighted in major resources. Conversely, many recommended tools were neither open source nor free despite the wide availability of open source alternatives providing the same service.
Key findings of the market analysis
Most Digital Security Guides are not Up-to-Date
Just like the tools they recommend, many digital security guides face a lack of funding and long-term maintenance. If resources for a guide were only allocated during a certain period or under a specific project (like SaferJourno, for example), it is unlikely that the organization behind it will have additional funding to maintain the guide. Other guides, like the Trainer’s Curriculum under LevelUp, were designed to be “community owned.” Ongoing community-driven maintenance often proves challenging due to lack of clear coordination among maintainers and the time constraints facing contributors.
These factors often result in out-of-date guides recommending tools that no longer exist or have been absorbed into newer tools. However, even if a guide is not updated, many of the best practices it recommends are likely to be relevant and useful. Fortunately, less formalized tool recommendations and guidelines are often provided through a variety of news sources. Through our market analysis research, we identified outlets such as Wired, Vice’s Motherboard series, and the Intercept which regularly publish articles that include newer tools.
Well-established and well-funded tools showed the greatest dominance within the market.
Tor, the second most cited tool in our market analysis, appeared in all of the guides surveyed. The Tor Project and Signal both have substantial annual budgets including grant funding, donations, and in the case of Signal, $50 million worth of funding from WhatsApp founder and Signal Foundation chairman Brian Acton.
The exception is KeePassXC, which is the only widely recognized open source option for a password manager and was the third-most highly cited tool in the digital security guides. Notably, the KeePassXC team is made up entirely of unpaid volunteers.
There are fewer digital security guides that cover new and emerging tools.
Tools that not only recorded consistent usership but were identified as commonly used among at-risk communities are not spotlighted in major resources. These tend to be tools with useful privacy and security options that are often too untested to be recommended. BASICS aims to resolve this by supporting the sourcing and vetting of these tools, in turn helping to improve coordination within the trainer and DigiSec guide community to recognize emerging tools.
Tools Mentioned in Guides are Not Accessible to Vulnerable Users
While some guides are translated into different languages, the tools they recommend are not always free or open source. Many of the VPNs recommended by guides from journalist safety organizations, for example, require a paid subscription. That leaves many vulnerable users, especially in the Global South, financially excluded from accessing what are deemed the most secure tools. Internews’ USABLE project is building feedback loops between digital security trainers, design experts, and open source developers to address this challenge.
Similarly, the guides reviewed for the market analysis did not include tools that can be accessed during Internet blackouts. The secure messaging app Briar, for example, is recommended from within the Internews network and has been known to operate in Kashmir during the shutdown. The region’s shutdown has been the longest ever recorded in a democracy. Most Briar users are in countries which are notorious for ongoing Internet censorship and human rights abuses (excepting Germany, which has a robust wireless and mesh community). Looking solely at the market analysis, in which it scored 0 mentions, one would wrongly conclude that Briar is neither a commonly used nor well-known tool among the DigiSec community.
Trainers deliberately avoid recommending guides
The team behind the USABLE project provided useful contextual information for this finding: one of the reasons digital security guides and trainers sometimes fail to recommend specific tools is due to concern on the part of trainers that any recommended tool may cease to be maintained, thus putting users at risk. Megan DeBlois, Information Security Advisor at Internews, further explained that the other main reason guides and/or trainers tend not to recommend specific tools is that tools alone don’t necessarily provide answers to all problems an activist might face online. Well-established tools like Signal and Tor, she pointed out, “may give users a false sense of security if used improperly.” Signal is a good example; many users of the app don’t always realize that phone numbers are linked to their real identities. When you use Signal, you’re therefore linking yourself to whomever you’re talking with if your adversary has access to the wire.
Conclusion
Ultimately, our takeaway from the process of creating the market analysis is reinforcement that the work of the BASICS project to improve sustainability of key open source security tools is an acute need within the digital security community. We also hope to encourage the OrgSec community to reflect on the manner in which digital security guides are developed, given the challenges we have highlighted around maintenance and keeping these guides up-to-date.
