A look at why threat information sharing is key to improving security among targeted populations.
First … what is threat information?
Threat information is a term used in the information security community to mean a variety of things. Everyone has their own definition (e.g. NIST definition), but the one we use for our threat information project at Internews is the following:
Knowledge or data that can help you protect yourself, your organization, or your community against someone who is attempting to cause harm.
Our definition is intentionally broad to encompass things such as:
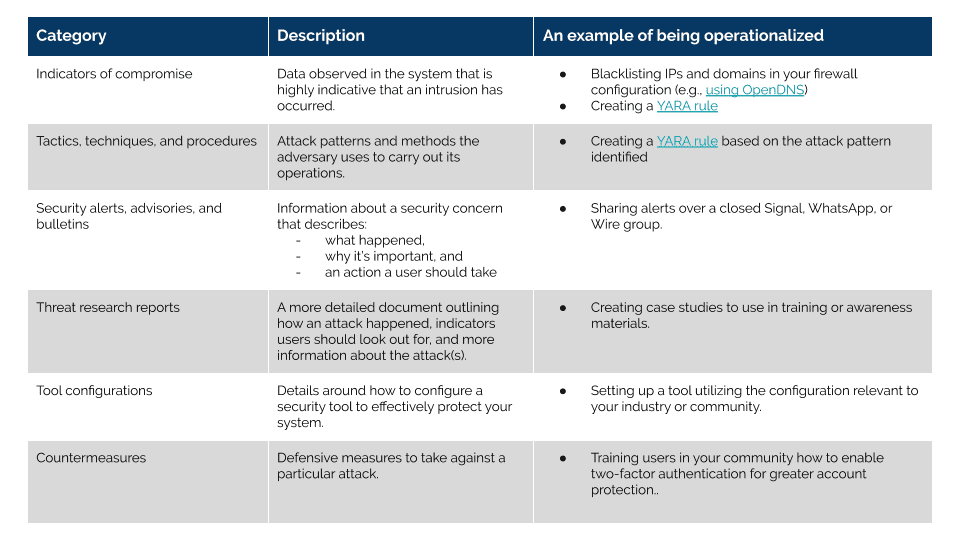
- Indicators of compromise
- Tactics, techniques, and procedures (TTPs)
- Security alerts, advisories, and bulletins
- Threat research reports (e.g. Citizen Lab, Amnesty, ThreatConnect, ESET)
- Tool configurations (e.g. Linux firewall setup and configuration)
- Countermeasures (e.g. Mitigations from MITRE ATT&CK)
All of this information can be shared through a variety of methods, from sharing with smaller, closed groups to sharing publicly. Decisions around when and who to share this information with is one that many threat researchers must decide on their own, using things such as the Traffic Light Protocol to help establish a common language among the threat research community around how the information may be used and shared beyond the trusted group.
How threat information is used in the real world
All of this threat information is great, but what does it look like in practice? Threat information is really only valuable if you can put it to work. This usually means you operationalize it in some way within your organization or community.
Some companies do this with their products to protect millions, if not billions, of users. For example, Google may notify, block, or remove malicious emails in your Gmail inbox if they’ve been identified as spear-phishing or prevent you from visiting a website because it’s infected with malware. These are examples of threat information in action with high impact on everyday users.
Why it’s important for human rights groups
Threat information sharing is critical to enhancing security for targeted populations like human rights groups in two key ways:
- Leveraging Protection from Products: Threat information sharing can help harden the systems and platforms at-risk and targeted populations are using everyday, from Gmail to WhatsApp to Twitter to Android. These products are often critical to human rights defenders’ work. Sharing threat information with private sector who can then develop integrations in their platforms protects all users of that product, including the at-risk communities experiencing the attack.
- Community Awareness: Threat alerts, reports, countermeasures, and configurations all help raise community-wide awareness where very little information is often known about the ways in which the adversary is targeting a community. When attacks do occur and we’re able to understand how they work, community members can better protect themselves and notify more broadly those who are likely to experience similar attacks.
Among the human rights community today, we need to work more closely with private sector in order to help harden the tools and technologies used by civil society around the globe, while also prioritizing our awareness raising efforts using evidence of attacks actively impacting the community. Understanding targeted attacks against human rights groups not only helps us protect them, but those attacks and patterns will likely be replicated and perpetrated against other user groups as well.
References
1. https://en.wikipedia.org/wiki/Indicator_of_compromise
2. https://azeria-labs.com/tactics-techniques-and-procedures-ttps
3. https://www.us-cert.gov/ncas/bulletins
4. https://www.us-cert.gov/tlp
5. https://csrc.nist.gov/glossary
Cover Image by Ifrah Yousuf / CC by 4.0
